
We Bring Light into Production Halls
OT Assessment
with OTORIO
With our assessment, we automatically visualize the entire inventory of OT, IoT, and IT assets in the OT environment using industrial and secure protocols and methods. Sounds difficult? It's not trivial either.
OT Requires Foundational Work
These Three Points are Essential
Establish Visibility
Legacy systems, missing asset management, grown structures: If we don't know what awaits us in the OT environment, we have no chance.
Consider Criticality
No company can afford a standstill in the OT environment, which is why we work with a digital twin for detection and identification. This ensures that there are no disruptions.
Environment and Compliance Assessment
We provide action recommendations regarding possible ransomware scenarios and compliance assessment with the goal of sustainably reducing risk.
We Work in a Secure Environment
Collect Data &
Create OT Twin
Our assessment includes the detection and identification of assets, machines, network segments, security configurations, reachability, and actual connectivity between devices. The asset inventory is contextualized according to roles, relationships to operational processes, and impacts. Subsequently, we create a digital cyber twin of the environment to analyze the security situation. This ensures that no impairment or interruption of operations can occur.


The importance of OT and IOT security in the context of digitalization cannot be overstated, as it ensures the fundamental integrity, availability, and reliability of operational technologies used in critical infrastructure, industrial processes, smart cities, and building digitalization.
Uwe Grunwitz
Head of OT-Security
What You Get From Us
for the Start
Critical attack vectors are identified in a way that points not only to vulnerabilities but also to preparation against ransomware and potential threats that can be triggered through the supply chain. For each risk, a guide with practical, step-by-step recommendations for risk minimization is created, tailored to the operational environment. The result provides a risk-based impact report, allowing security experts to focus on the highest priority work.
The assessment also provides out-of-the-box compliance evaluations for industrial security standards such as IEC 62443, NIST, and NERC CIP, from individual assets to the entire operational environment. Thus, our assessment delivers an overall conformity assessment, clear and detailed information about deviations, and recommendations and guidelines for addressing these deviations.
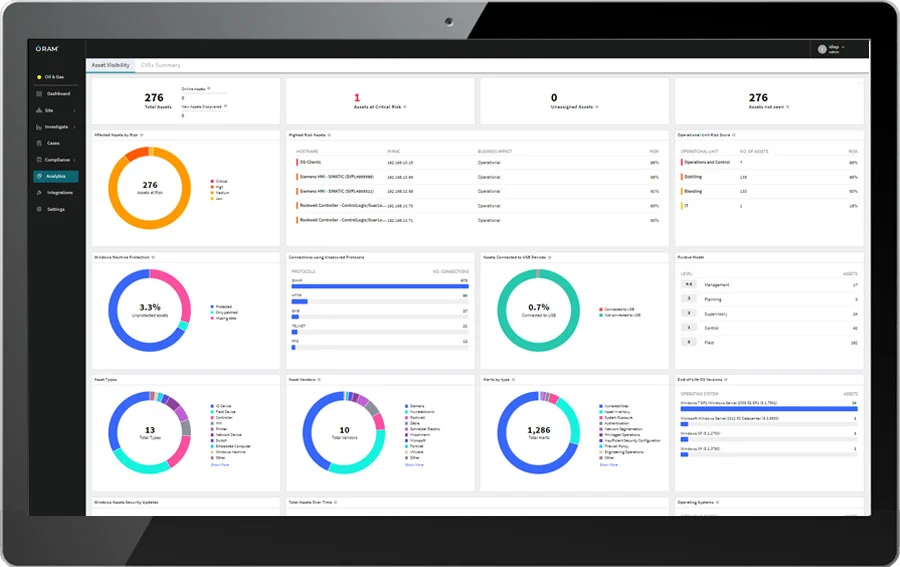
Asset Visibility from OTORIO
Strategic Partnership
in OT
We are glad to have found a strategic partner in OTORIO for the OT sector. At OTORIO, OT is not just in the name, but especially in the DNA. With the Asset Visibility Tool, we create unrivaled transparency in any OT environment. Regardless of which components, protocols, manufacturers, or operation-specific data - the tool's claim is to find and provide everything. Sounds too good to be true? Let's find out together.
Whitepaper
OT Security Reimagined:
Context-Based Exposure Management for Direct Results
In this whitepaper you'll learn:
- How to precisely identify risks in complex OT environments
- Why context-based security strategies are crucial
- Which modern technologies optimize your protection


